In this post I will be explaining the lab I was given to complete with steps and screenshots on how to complete them. I was instructed to
-Take over the victim’s connection using Kali Linux
-After you taking over, try to ping previous websites from the victim and make sure if the IPs already changed to Kali’sIP
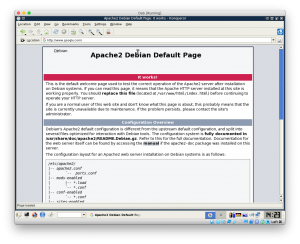
-From the Victim, try to open websites and make sure that you can see the fake website not the real one.
-Record every activities you perform with screenshot (video is a plus)
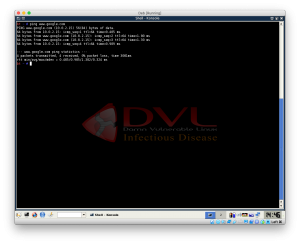
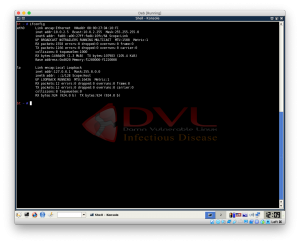
1.Find IP of your machine
2.Find IP of victim’s machine
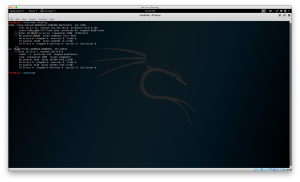
3.Make file containing your machine’s IP and the domain you want to intercept
4.Start apache server
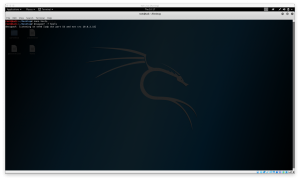
5.Start dnsspoof
6.Access domain from victim machine
7.Compare IP address of real domain and spoofed domain (Real google IP: 8.8.8.8)